This is an old revision of the document!
Table of Contents
Log4Shell Vulnerability
Log4Shell (CVE-2021-44228) is a remote-code-execution (RCE) vulnerability, meaning it can force your computer to run any arbitrary Java code.
Anyone can exploit this vulnerability by simply typing a special message into the Minecraft chat.
If you are playing on a Minecraft server and your Minecraft installation is vulnerable (even if the server is patched), then another player could, for example, install a virus on your computer by simply sending you a chat message.
Log4Shell is caused by certain versions of the Log4j library, which are included in Minecraft 1.7 - 1.18. Both Minecraft clients and Minecraft servers can be vulnerable to this exploit.
Affected Wurst versions
| Wurst MC Version | Status | Patched by | How to fix |
|---|---|---|---|
| Wurst MC 1.18.1 | Not affected | Relax, you're good.  |
|
| Wurst MC 1.18 | Patched | Fabric Loader v0.12.10 | Reinstall Fabric. |
| Wurst MC 1.17.x | Patched | Fabric Loader v0.12.10 | Reinstall Fabric. |
| Wurst MC 1.16.x | Patched | Fabric Loader v0.12.10 | Reinstall Fabric. |
| Wurst MC 1.15.x | Patched | Fabric Loader v0.12.10 | Reinstall Fabric. |
| Wurst MC 1.14.x | Patched | Fabric Loader v0.12.10 | Reinstall Fabric. |
| Wurst MC 1.12.x | Patched | Wurst v6.35.2 | Update Wurst. |
| Wurst MC 1.11.x | Vulnerable | Do not use in multiplayer. | |
| Wurst MC 1.10.x | Vulnerable | Do not use in multiplayer. | |
| Wurst MC 1.9.x | Vulnerable | Do not use in multiplayer. | |
| Wurst MC 1.8.x | Patched | Wurst v6.35.2 | Update Wurst. |
| Wurst MC 1.7.x | Vulnerable | Do not use in multiplayer. |
Note: MultiMC has released their own patch for the Log4Shell exploit. If you are using MultiMC, you might be fine even with a vulnerable Wurst version, but you should do a test in singleplayer to be sure.
How to check your Fabric Loader version
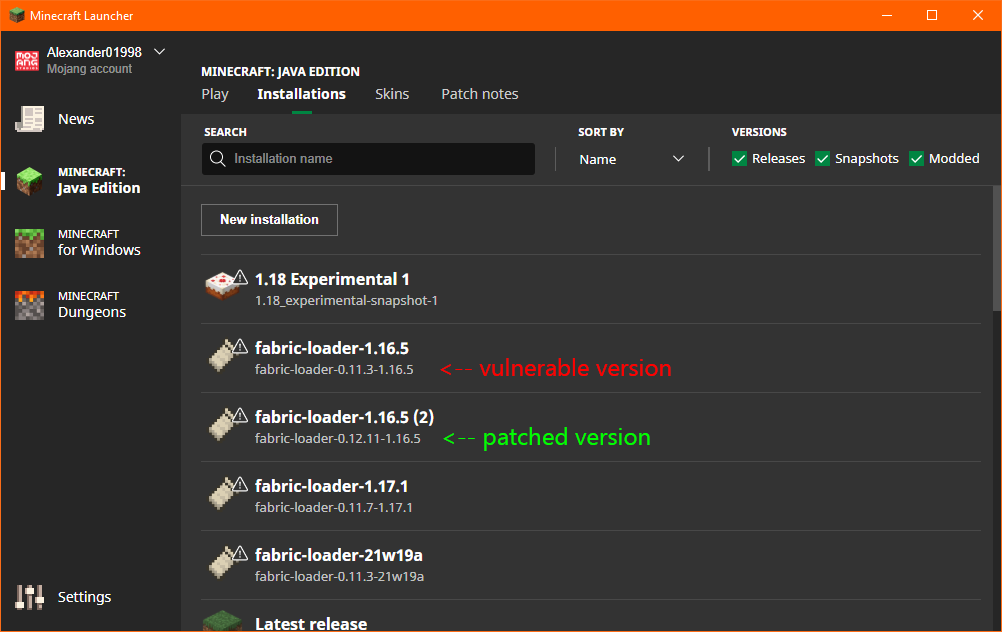
Official Launhcer
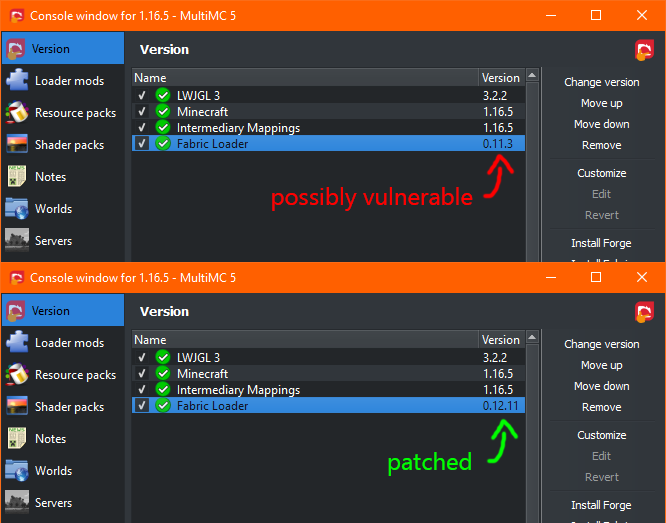
MultiMC
Click on “Edit Instance” and check what it says next to “Fabric Loader”:
Note: MultiMC has released their own patch for the Log4Shell exploit. You might be fine even with an older Fabric Loader version, but you should do a test in singleplayer to be sure.
How to test if you are affected
Open the Minecraft chat and enter the following message:
${jndi:ldap://127.0.0.1/a}
Then check your log file (default: %appdata%/.minecraft/logs/latest.log).
If your Minecraft installation is vulnerable, you will see a a long error like this in the logs:
[17:32:25] [Client thread/INFO]: [CHAT] <Player671> ${jndi:ldap://127.0.0.1/a}
2021-12-11 17:32:29,077 Client thread WARN Error looking up JNDI resource [ldap://127.0.0.1/a]. javax.naming.CommunicationException: 127.0.0.1:389 [Root exception is java.net.ConnectException: Connection refused: connect]
at com.sun.jndi.ldap.Connection.<init>(Connection.java:243)
at com.sun.jndi.ldap.LdapClient.<init>(LdapClient.java:137)
at com.sun.jndi.ldap.LdapClient.getInstance(LdapClient.java:1615)
at com.sun.jndi.ldap.LdapCtx.connect(LdapCtx.java:2849)
at com.sun.jndi.ldap.LdapCtx.<init>(LdapCtx.java:347)
at com.sun.jndi.url.ldap.ldapURLContextFactory.getUsingURLIgnoreRootDN(ldapURLContextFactory.java:60)
at com.sun.jndi.url.ldap.ldapURLContext.getRootURLContext(ldapURLContext.java:61)
at com.sun.jndi.toolkit.url.GenericURLContext.lookup(GenericURLContext.java:202)
at com.sun.jndi.url.ldap.ldapURLContext.lookup(ldapURLContext.java:94)
at javax.naming.InitialContext.lookup(InitialContext.java:417)
at org.apache.logging.log4j.core.net.JndiManager.lookup(JndiManager.java:129)
at org.apache.logging.log4j.core.lookup.JndiLookup.lookup(JndiLookup.java:54)
at org.apache.logging.log4j.core.lookup.Interpolator.lookup(Interpolator.java:183)
at org.apache.logging.log4j.core.lookup.StrSubstitutor.resolveVariable(StrSubstitutor.java:1054)
at org.apache.logging.log4j.core.lookup.StrSubstitutor.substitute(StrSubstitutor.java:976)
at org.apache.logging.log4j.core.lookup.StrSubstitutor.substitute(StrSubstitutor.java:872)
at org.apache.logging.log4j.core.lookup.StrSubstitutor.replace(StrSubstitutor.java:427)
at org.apache.logging.log4j.core.pattern.MessagePatternConverter.format(MessagePatternConverter.java:127)
at org.apache.logging.log4j.core.pattern.PatternFormatter.format(PatternFormatter.java:38)
at org.apache.logging.log4j.core.layout.PatternLayout$PatternSerializer.toSerializable(PatternLayout.java:333)
at org.apache.logging.log4j.core.layout.PatternLayout.toText(PatternLayout.java:232)
at org.apache.logging.log4j.core.layout.PatternLayout.encode(PatternLayout.java:217)
at org.apache.logging.log4j.core.layout.PatternLayout.encode(PatternLayout.java:57)
at org.apache.logging.log4j.core.appender.AbstractOutputStreamAppender.directEncodeEvent(AbstractOutputStreamAppender.java:177)
at org.apache.logging.log4j.core.appender.AbstractOutputStreamAppender.tryAppend(AbstractOutputStreamAppender.java:170)
at org.apache.logging.log4j.core.appender.AbstractOutputStreamAppender.append(AbstractOutputStreamAppender.java:161)
at org.apache.logging.log4j.core.appender.RollingRandomAccessFileAppender.append(RollingRandomAccessFileAppender.java:218)
at org.apache.logging.log4j.core.config.AppenderControl.tryCallAppender(AppenderControl.java:156)
at org.apache.logging.log4j.core.config.AppenderControl.callAppender0(AppenderControl.java:129)
at org.apache.logging.log4j.core.config.AppenderControl.callAppenderPreventRecursion(AppenderControl.java:120)
at org.apache.logging.log4j.core.config.AppenderControl.callAppender(AppenderControl.java:84)
at org.apache.logging.log4j.core.config.LoggerConfig.callAppenders(LoggerConfig.java:448)
at org.apache.logging.log4j.core.config.LoggerConfig.processLogEvent(LoggerConfig.java:433)
at org.apache.logging.log4j.core.config.LoggerConfig.log(LoggerConfig.java:417)
at org.apache.logging.log4j.core.config.LoggerConfig.log(LoggerConfig.java:403)
at org.apache.logging.log4j.core.config.AwaitCompletionReliabilityStrategy.log(AwaitCompletionReliabilityStrategy.java:63)
at org.apache.logging.log4j.core.Logger.logMessage(Logger.java:146)
at org.apache.logging.log4j.spi.AbstractLogger.logMessageSafely(AbstractLogger.java:2091)
at org.apache.logging.log4j.spi.AbstractLogger.logMessage(AbstractLogger.java:2005)
at org.apache.logging.log4j.spi.AbstractLogger.logIfEnabled(AbstractLogger.java:1876)
at org.apache.logging.log4j.spi.AbstractLogger.info(AbstractLogger.java:1421)
at net.minecraft.client.gui.GuiNewChat.printChatMessageWithOptionalDeletion(GuiNewChat.java:157)
at net.minecraft.client.gui.GuiNewChat.printChatMessage(GuiNewChat.java:140)
at net.minecraft.client.gui.chat.NormalChatListener.func_192576_a(NormalChatListener.java:18)
at net.minecraft.client.gui.GuiIngame.func_191742_a(GuiIngame.java:1319)
at net.minecraft.client.network.NetHandlerPlayClient.handleChat(NetHandlerPlayClient.java:813)
at net.minecraft.network.play.server.SPacketChat.processPacket(SPacketChat.java:53)
at net.minecraft.network.play.server.SPacketChat.processPacket(SPacketChat.java:1)
at net.minecraft.network.PacketThreadUtil$1.run(PacketThreadUtil.java:15)
at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:511)
at java.util.concurrent.FutureTask.run(FutureTask.java:266)
at net.minecraft.util.Util.runTask(Util.java:47)
at net.minecraft.client.Minecraft.runGameLoop(Minecraft.java:1133)
at net.minecraft.client.Minecraft.run(Minecraft.java:428)
at net.minecraft.client.main.Main.main(Main.java:115)
at Start.main(Start.java:11)
Caused by: java.net.ConnectException: Connection refused: connect
at java.net.DualStackPlainSocketImpl.connect0(Native Method)
at java.net.DualStackPlainSocketImpl.socketConnect(DualStackPlainSocketImpl.java:79)
at java.net.AbstractPlainSocketImpl.doConnect(AbstractPlainSocketImpl.java:350)
at java.net.AbstractPlainSocketImpl.connectToAddress(AbstractPlainSocketImpl.java:206)
at java.net.AbstractPlainSocketImpl.connect(AbstractPlainSocketImpl.java:188)
at java.net.PlainSocketImpl.connect(PlainSocketImpl.java:172)
at java.net.SocksSocketImpl.connect(SocksSocketImpl.java:392)
at java.net.Socket.connect(Socket.java:607)
at java.net.Socket.connect(Socket.java:556)
at java.net.Socket.<init>(Socket.java:452)
at java.net.Socket.<init>(Socket.java:229)
at com.sun.jndi.ldap.Connection.createSocket(Connection.java:380)
at com.sun.jndi.ldap.Connection.<init>(Connection.java:220)
... 55 more
If your Minecraft installation is not vulnerable, you will simply see the chat message in the logs:
[17:37:50] [Server thread/INFO]: <Player578> ${jndi:ldap://127.0.0.1/a}
[17:37:50] [Client thread/INFO]: [CHAT] <Player578> ${jndi:ldap://127.0.0.1/a}